DDoS Attacks: Taxonomy, Targets, and Tactics

Introduction to DDoS Attacks
What is a DDoS (Distributed Denial of Service) Attack?
A cyber attack, it’s like blocking an internet server or website with lots of data generated from infected computers. This leads to the slow down or shut of the website or internet server making it difficult for the genuine user to use the services of the particular server or website. This can be performed using many ways, but the idea remains the same i.e. to overload the website with too much traffic.
Taxonomy of DDoS attack
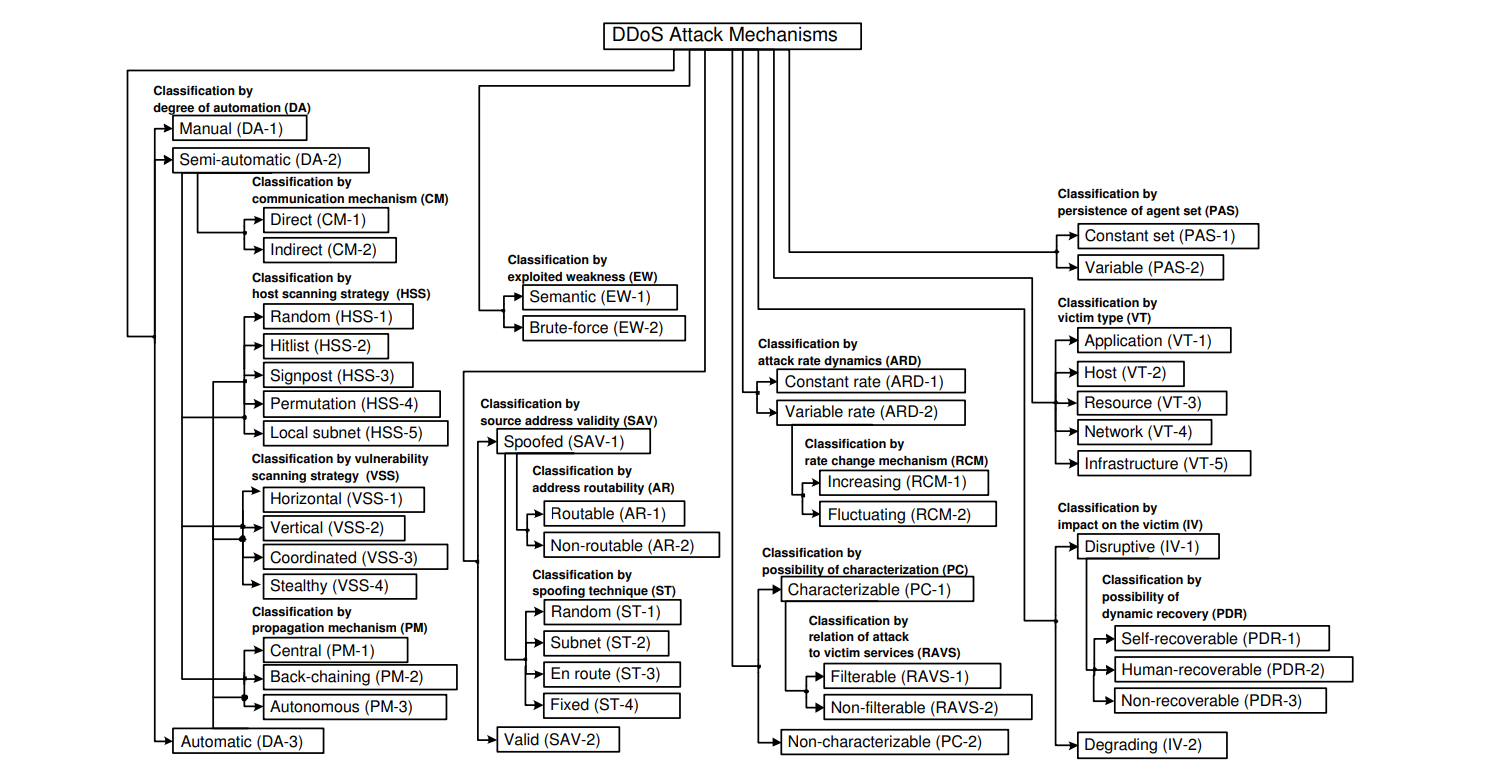
Based on the Degree of automation, exploited weakness, source address validity, attack Rate Dynamics, Possibility of Characterization, Persistence of Agent Set, and Impact on the Victim, we can classify them, let study each one of them.
Degree of Automation
Every phase starting from recruit, exploit, infect, and use phases can be done automated or manually, so based on the degree of automation DDoS attack can be classified as:
Manual DDoS Attacks
When the complete DDoS attack is done manually that is without the use of any automated tools. In this starting from finding vulnerable computers to installing attacking tools and launching the attack everything is done manually, This is common to use when the user is new to DDoS attack.
Semi-Automatic DDoS Attacks
Here some of the tasks are completed using automated tools while the others are still done manually. Automated tools are used to find vulnerable computers and infect them like recruiting them in a network of attack machines. The rest of the tasks i.e. launching the attack by giving certain instructions are still done manually.
Automatic DDoS Attacks
Here everything is done by the automated tools without involving any major manual work. Starting from finding vulnerable computers to finding attack tools and launching the attack. The attackers set everything before the attacks i.e. mentioning the time of the attack, how long the attack lasted, and who is the attack, it will automatically start at the mentioned time without any immediate instructions.
Exploited Weakness to Deny Service
This type of attack mainly focuses on the services of the target which means attackers focus on the services that are provided by the target to their users. This can be done in two ways:
Semantic Attacks
This attack specifically messes up a particular target’s software or system to make them use a lot of resources. This can be done by filling the queue with a lot of fake connections. This can be stopped by using filters and fixing the problems of the software. However, this can cause a big problem.
Brute-Force Attacks
This attack overwhelms the targets by sending tons of data and normal requests and quickly uses up the space. This is not easy to resolve as the requests that attackers send seem to be normal requests.
Source Address Validity
Attackers may use fake or actual addresses to attack the target. On this basis, we have two types:
Spoofed Source Address
The attackers fake the source address on the attack packets, which makes the detection and chance of being caught very less.
Valid Source Address
The attacker uses the real source address. This can be used for certain types of attacks when specific applications or protocols are targeted and communication between the attacker and victim happens. This is usually done when the operating system doesn’t have a good way to change the packet headers like old versions of Windows.
Attack Rate Dynamics
This type of attack mainly focuses on the rate at which the machine sends the requests. This can be further divided into two types:
Constant Rate
In this type of attack, machines keep sending the requests or attack packets at a constant rate as the attack starts. This is the cheaper method and immediately messes up the victim’s services. It can be easily identified because of the unusual traffic.
Variable Rate
In this type of attack, machines send the attack packet at a variable speed according to the activity of the victim or programmed patterns. Machines stop and start at specific times. If all the machines do this together it will make the victim’s server go up and down periodically.
Possibility of Characterization
In this type of attack, we can classify and recognize the attack based on the information that packets carry. This can be used to make certain rules and filters to protect from particular types of attacks. This can be further classified as:
Characterizable Attacks
The attack specifically targets specific parts of the victim such as IP and transport protocol headers or the content of the packets. this can be further divided into
- Filterable Attacks: These attacks use messed-up packets or target non-critical parts of the victim's system, so we can use a firewall to filter them out. For example, attacks flooding a Web server with too many UDP or ICMP packets.
- Non-Filterable Attacks: These attacks use normal-looking packets that ask for real and important services from the victim's system. It's hard to filter them without blocking legitimate traffic. For example, flooding a Web server with too many HTTP requests or a name server with too many DNS requests.
Non-Characterizable Attacks
These attacks try to mess with the victim's network by sending all kinds of packets to different parts of its system. It's tough to figure out what kind of attack it is because it's all mixed up. How we classify these attacks depends on how much time and effort we can spend figuring them out.
Persistence of Agent Set
The "Persistence of Agent Set" in DDoS attacks refers to how the group of attacker machines (agents) changes over time during an attack. This variation helps attackers avoid being caught and makes it harder to trace the source of the attack. There are two main categories based on this persistence:
- Constant Agent Set (PAS-1): In this type of attack, all attacker machines behave similarly and are active at the same time during the attack. They all follow the same instructions and work together. Examples include all machines attacking at once or a pulsing attack where they all have the same "on" and "off" periods.
- Variable Agent Set (PAS-2): Here, the attacker divides the available machines into different groups. Only one group attacks at a time, while others remain inactive. It's like a military strategy where different units attack at different times and places. Machines might switch between groups, and groups might become active again after a break.
This concept shows that DDoS attacks are dynamic, and defense mechanisms need to adapt to the changing set of attacker machines during an attack to effectively counter them.
Victim Type
"Victim Type" in the realm of DDoS attacks refers to how we classify the target of the attack based on what kind of service it is affecting. Here are the main classes:
- Application: This is when the attack goes after specific applications, like web servers or email services.
- Host: These attacks target individual machines or hosts in a network, messing with their ability to work properly.
- Network : Here, the attack targets the network itself, messing with connectivity and network services.
- Infrastructure: This class is about attacks hitting critical parts of the network infrastructure, like DNS servers or routers.
These categories help us understand what exactly is being targeted in a DDoS attack. This knowledge helps in building defense mechanisms that can protect against attacks on different types of victims.
Impact on the Victim
"Victim Type" in the realm of DDoS attacks refers to how we classify the target of the attack based on what kind of service it is affecting. Here are the main classes:
- Application: This is when the attack goes after specific applications, like web servers or email services.
- Host : These attacks target individual machines or hosts in a network, messing with their ability to work properly.
- Network : Here, the attack targets the network itself, messing with connectivity and network services.
- Infrastructure : This class is about attacks hitting critical parts of the network infrastructure, like DNS servers or routers.
These categories help us understand what exactly is being targeted in a DDoS attack. This knowledge helps in building defense mechanisms that can protect against attacks on different types of victims.
Conclusion
Understanding these classifications helps in developing defense mechanisms tailored to protect against different types of DDoS attacks, considering the dynamic nature of attack tactics and targets.