Comprehensive Guide on DDoS Attacks

Introduction to DDoS Attacks
What is a DDoS (Distributed Denial of Service) Attack?
A cyber attack, it’s like blocking an internet server or website with lots of data generated from infected computers. This leads to the slow down or shut of the website or internet server making it difficult for the genuine user to use the services of the particular server or website. This can be performed using many ways, but the idea remains the same i.e. to overload the website with too much traffic.
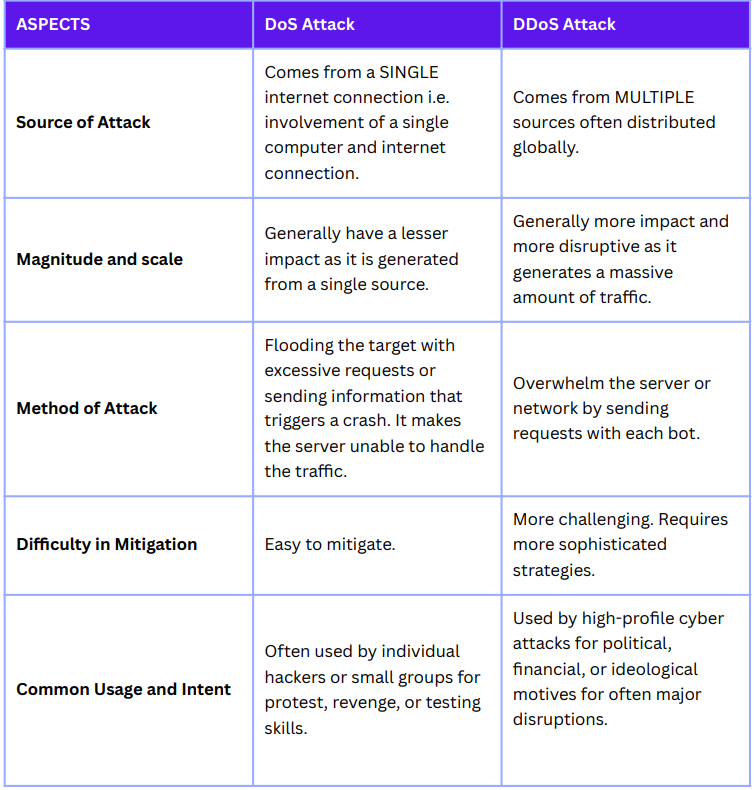
DDoS vs. DoS: Understanding the Differences
The Evolution of DDoS Attacks
- Early DDoS Attacks (Late 1990s): DDoS attacks started with single scripts(allowed attackers to command multiple hosts to flood a victim with traffic) that listened to IRC channels.
- Command and Control Networks (Late 1990s): Dedicated command and control networks like shaft, Trinoo, and tribe Flood network emerged, making DDoS attacks more sophisticated.
- Code Red and MyDoom Worms (2001-2003): Notable worms like Code Red and MyDoom marked a new era in DDoS attacks by targeting specific victims.
- Botnets (Early 2000s): Botnets like Agobot, Nesebot, Spybot, and RxBot were common, and the Kaiten botnet codebase was often used for DDoS attacks.
- Shift from IRC-Based Botnets (2006): Shift occurred from IRC Botnets to more specialized tools for DDoS attacks, such as peer-to-peer stormworms, etc.
How DDoS Attacks Work
The Mechanics of a DDoS Attack
- Compromising Multiple Systems: To gain control the attacker starts exploiting vulnerabilities in computers and these computers become a part of a botnet. This can done through malware, security vulnerabilities, etc.
- Creating a Botnet: Once the attacker infects the computer using malicious activities. It becomes the Botnet and can be remotely controlled by the attacker.
- Launching the Attack: Now the attacker uses the botnet to send a massive amount of data or requests in the form of requests for access, messages, or fake packets to the target’s network or server.
- Overwhelming the Target: Massive amount of data or requests slow down the services or may shut down the services.
Botnets and Their Role in DDoS
A hacker controls the infected devices using a network known as Botnet. Bots form a network and bots are numerous and spread across the globe.
Botnets are formed when malware infects the computer and once it gets infected it acts as a bot without the owner’s knowledge. These malware are phishing Emails, malicious websites, etc.
Role in DDoS Attacks: The volume of traffic to shut down or slow down the server is generated by Bots in the botnet by sending massive amounts of requests or messages to the server.
Common Techniques Used in DDoS Attacks
DDoS attacks use many techniques to overwhelm the targeted system. some of them are listed here:
- Volumetric Attacks: The most common Attack, focuses on saturating the bandwidth of the targetted site by sending a massive amount of data. This includes:
- UDP Flood: Using user datagram protocol packets attacker attacks the random port on a remote host.
- ICMP (Internet Control Message Protocol) Flood: The attacker overwhelms the target with the ping requests.
- Amplification Attacks: Reflecting attacker’s traffic off other networks to increase the amount of data sent to the target. eg.- DNS amplification attack.
- Protocol Attacks: Consume Server resources or bandwidth of targeted server, mainly attacks transport or network layer protocols.
- SYN (synchronization) Flood: The attacker continuously sends the SYN request but does not completely establish the connection
- Ping of Death: for destabilizing the target large pings are sent.
- Application Layer Attacks: This attack is difficult to detect as it mimics the original requests and aims to exhaust application resources. This includes:
- HTTP(Hypertext Transfer Protocol) Flood: To overload the server numerous HTTP requests are sent.
- Slowloris: Keeping the connection to the target server open and slow which leads to overloading the server.
- Zero-day DDoS: Exploiting vulnerabilities in software that are unknown or have no current fix.
- Multi-Vector Attacks: This is the combined attack, volumetric attacks, protocol attacks, and applications layer attacks simultaneously.
- IoT-Based Attacks: With the proliferation of Internet of Things (IoT) devices, attackers increasingly exploit poorly secured IoT devices to create powerful botnets for large-scale DDoS attacks.
- Peer-to-Peer Attacks: Instead of using a traditional botnet, these attacks coerce legitimate users of peer-to-peer file-sharing services to send requests to the target.
Types of DDoS Attacks
There are several types of DDoS attacks, such as:
- Volume-based attacks: This aims to saturate the bandwidth of the attacked site using ICMP floods, UDP floods, etc.
- Protocol attacks: This aims to exploit server resources or firewall and load balancer capacity using SYN floods, Pings of Death, etc.
- Application layer attacks: This aims to crash the web server through application calls using low and slow attacks, and GET/POST floods.
Identifying and Diagnosing DDoS Attacks
Symptoms of a DDoS Attack
DDoS attacks can be difficult to identify as they resemble non-malicious issues at times, however, some of the symptoms can indicate a DDoS attack:
- Unusually Slow Network Performance: Includes slower access to the website and difficulty in accessing the server as it slows down the network performance
- Intermittent Website and Network Disruptions: The website becomes unavailable and returns to go down this goes on repeatedly.
- Excessive Amount of Spam Emails: A sudden large number of spam Emails can be a sign of an email server being targeted.
- Unavailability of a Particular Website: everything on the internet is working fine except the specific website or server that is targeted.
- Unexpected Traffic from Unknown IPs: A large amount of traffic from unfamiliar IPs.
- Overloaded Server: without the increase in genuine users large amount of traffic is generated
- Unexplained Connection Requests: A large amount of connection requests.
- Increased Requests for a Single Page or Endpoint: Receiving requests for a particular page or endpoint.
- Unusual Traffic Patterns: Any atypical traffic pattern, like coming from a single geographical location or IP range.
Tools for Detecting DDoS Attacks
DDoS Attacks can be detected using specialized tools and systems. These can help in identifying attacks and play a major role in mitigating their impact.
- Intrusion Detection Systems (IDS):
- Snort: It is capable of performing real-time traffic analysis and packet logging on IP networks.
- Suricata: Another open-source network IDS, Intrusion Prevention System (IPS), and Network Security Monitoring (NSM) engine.
- Network Traffic Analysis Tools:
- Wireshark: widely used network protocol analyzer that helps in capturing and analyzing the network traffic in real-time.
- SolarWinds Network Performance Monitor: A comprehensive network performance monitor that can detect unusual network activity indicative of a DDoS attack.
- Web Application Firewall (WAF):
- Cloudflare: Offers DDoS protection and traffic filtering capabilities, which can help mitigate application-layer DDoS attacks.
- AWS Shield: A managed DDoS protection service that safeguards applications running on AWS.
- DDoS Protection and Mitigation Services:
- Akamai Prolexic: Provides cloud-based protection for applications and data centers.
- Radware DefensePro: A real-time network attack prevention device that protects against DDoS attacks, network intrusions, and malware propagation.
- Load Balancers:
- F5 BIG-IP Local Traffic Manager: It can distribute traffic evenly across servers and mitigate DDoS attacks by rerouting malicious traffic.
- NGINX: Often used for load balancing, NGINX can also help mitigate DDoS attacks by controlling the flow of traffic.
- Anomaly Detection Systems:
- NetFlow/SFlow Collectors: These systems analyze flow data generated by routers and switches to identify traffic patterns that may indicate a DDoS attack.
- AI/ML-Based Anomaly Detection: Advanced solutions that use artificial intelligence and machine learning algorithms to detect and respond to abnormal traffic patterns.
- Managed DDoS Protection Services:
- Verizon Digital Media Services: Offers a cloud-based DDoS shield that is part of their edge network services.
- Neustar UltraDDoS Protect: A cloud-based solution offering scalable protection against DDoS attacks.
Best Practices for DDoS Prevention
The prevention of DDoS attacks requires more than one layer of protection. We can’t completely vanish DDoS attacks but at least we can reduce them by adopting some of the best practices listed below:
- Implement Network Security Basics:
- Keep your systems and software updated with the latest security patches.
- Keep firewall installed and updated.
- Use antivirus and anti-malware to protect against malicious software.
- Enhance Network Infrastructure:
- Overprovision bandwidth to absorb some level of excess traffic.
- Implement redundancy for critical components to ensure network resilience.
- Employ load balancing to distribute traffic evenly across multiple servers.
- Deploy a Web Application Firewall (WAF):
- For filtering incoming traffic use WAFs for web applications, blocking malicious requests.
- Use Content Delivery Networks (CDNs):
- To make DDoS attackers difficult to accomplish their tasks use CDNs which can distribute the content of the website.
- Implement Rate Limiting:
- To prevent overload limit the request on a server that can be accepted over a certain time.
- Monitor and Analyze Traffic:
- Regularly check the network traffic to identify any spikes that could mark a DDoS attack.
- Use an intrusion detection system for real-time monitoring.
- Create a DDoS Response Plan:
- Have a clear idea and plan to respond to DDoS attacks which may include communication protocols and steps to mitigate the attack.
- Have the response plan updated.
- Leverage Cloud-Based DDoS Protection Services:
- For scalable defense mechanisms against large-scale DDoS attacks use cloud-based DDoS protection.
- Secure Network Perimeter:
- To protect against IP spoofing and route hijacking implement border gateway protocols
- Implement border gateway protocol (BGP) routing and IP filtering to defend against IP spoofing and route hijacking.
- Collaborate with Your ISP and Hosting Provider:
- Add services like traffic rerouting, scrubbing services, or additional bandwidth during an attack for additional support and protection by your hosting provider and internet service provider.
DDoS Protection Solutions
Safeguarding networks, websites, and online services is very important. These solutions can be hardware tools, software, and cloud-based services. Some of them are listed:
- Web Application Firewalls (WAFs):
- Purpose: Filter and monitor HTTP traffic between web applications and the internet.
- Examples: Cloudflare WAF, Imperva Incapsula, AWS WAF.
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS):
- Purpose: Often used as a part of a layered defense strategy. It monitors network traffic for policy violations and activities.
- Examples: Snort, Suricata.
- Content Delivery Networks (CDNs):
- Purpose: CDNs make attackers difficult to tackle as the content of the website is spread across multiple servers globally.
- Examples: Akamai, Cloudflare, Amazon CloudFront.
- DoS/DDoS Mitigation Appliances:
- Purpose: On-premises or cloud-based appliances specifically designed to detect and mitigate DDoS attacks.
- Examples: Radware DefensePro, Arbor Networks APS (NETSCOUT).
- Cloud-based DDoS Protection Services:
- Purpose: These services are used to absorb and mitigate the large-scale traffic of DDoS attacks
- Examples: Microsoft Azure's DDoS Protection, Google Cloud Armor, and AWS Shield.
- Hybrid DDoS Protection:
- Purpose:
- Combine on-premises hardware and cloud-based services to provide a comprehensive protection solution, ensuring immediate on-premises mitigation with the backup of cloud-based scalability.
- Examples: Combining solutions like an on-premises Radware DefensePro with a cloud-based service like Cloudflare.
- Traffic Analyzers and Network Monitors:
- Purpose: Monitor network traffic to identify anomalies that might indicate a DDoS attack.
- Examples: Wireshark, SolarWinds Network Performance Monitor.
- DDoS Protection as a Service (DPaaS):
- Purpose: A third-party service provider offers DDoS protection as a service, which can be a cost-effective and efficient solution for businesses without the resources to manage their own DDoS protection.
- Examples: Neustar UltraDDoS Protect, F5 Silverline DDoS Protection.
- DNS Routing:
- Purpose: Some services use DNS routing mechanisms to distribute and manage traffic, which can be effective in mitigating DDoS attacks.
- Examples: Services offered by DNS providers like Dyn or Google Cloud DNS.
- Anomaly Detection Systems:
- Purpose: Use AI and machine learning to detect unusual patterns in network traffic that could indicate a DDoS attack.
- Examples: Systems integrated within broader network management solutions.
Conclusion
DDoS attacks bring instability and unreliability of online services, affecting businesses and users all over the world. Its evolution has started from simple to complex and highly disruptive actions. Implementing detection systems, robust mitigation techniques, and opting for best practices can help us to safeguard ourselves from DDoS attacks.