SSL vs. SSH: Understanding the Differences and Similarities

Introduction
In today’s world as everything is on the Internet keeping every data safe is very important and at the same time a task to keep large amounts of data safe. For helping us in doing so we have SSL and SSH. SSL and SSH both ensure the confidentiality and integrity of data transmitted, but they work differently and in different layers. Let’s know more about them.
What Is SSL?
SSL, Secure Socket Layer is designed to provide a secure channel to communicate between client and server over the internet in the form of encrypted data which can only be decrypted by someone who owns a key. These keys can be symmetric or public. This usually involves handshaking protocol to establish a secure connection before communication initiates. It operates between the transport layer and the application layer.
How SSL Works
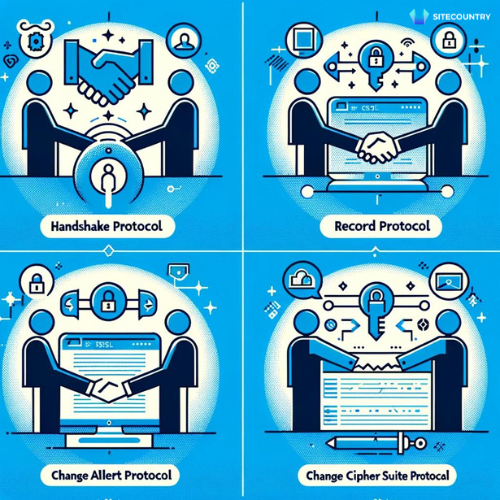
SSL protocol consists of 4 main protocols:
- Handshake Protocol- It Facilitates the secure establishment of sessions between the client and server, this involves exchanging of certificates and session key generation.
- Record Protocol- Once a secure session is established, record protocols ensure the data is encrypted and decrypted securely.
- Alert Protocol-Alert protocol ensures and communicates any error during data transfer.
- Change Cipher Suite Protocol-This protocol signals a switch to a new cypher suite for encryption
What Do You Use SSL For?

SSL is mainly used when maintaining data integrity and confidentiality is essential, for example in online banking, email and e-commerce. The protocol has endpoint authentication through digital certificates.
What Is SSH?
SSH, Secure Shell is a cryptographic network protocol. It is mainly used for secure remote login from one computer to another. It enables users to execute server commands remotely, transfer files, and navigate the server’s filesystem and many more. SSh ensures that all the communication between the server and client is encrypted as it uses various encryption techniques.
How SSH Works
SSH works on a client-server model. It can be done in various steps mentioned below:
- Connection Establishment- The SSH client initiates a connection to the SSH server. the server responds with details and supported cypher types.
- Server Authentication-Client verifies the server, if the connection is established for the first time then the client may ask for the verification of the digital signature.
- User Authentication- Using Passwords, Public Key authentication, and Kerberos server authenticates itself once the client is authenticated.
- Session Encryption- After successful authentication, a secure encrypted session is established using various algorithms.
- Data Transfer- Once the secure channel is established, data can be transferred between the client and server. The data include command execution results, file transfer, and terminal emulation data.
What Do You Use SSH For?

It plays an important role in the secure administration of systems and networks, data protection, and compliance with security policies and regulations. It is used in Remote Server Management, Secure File Transfer, Port Forwarding and Tunneling, Automating Remote Tasks and VPN over SSH.
Key Differences Between SSL and SSH
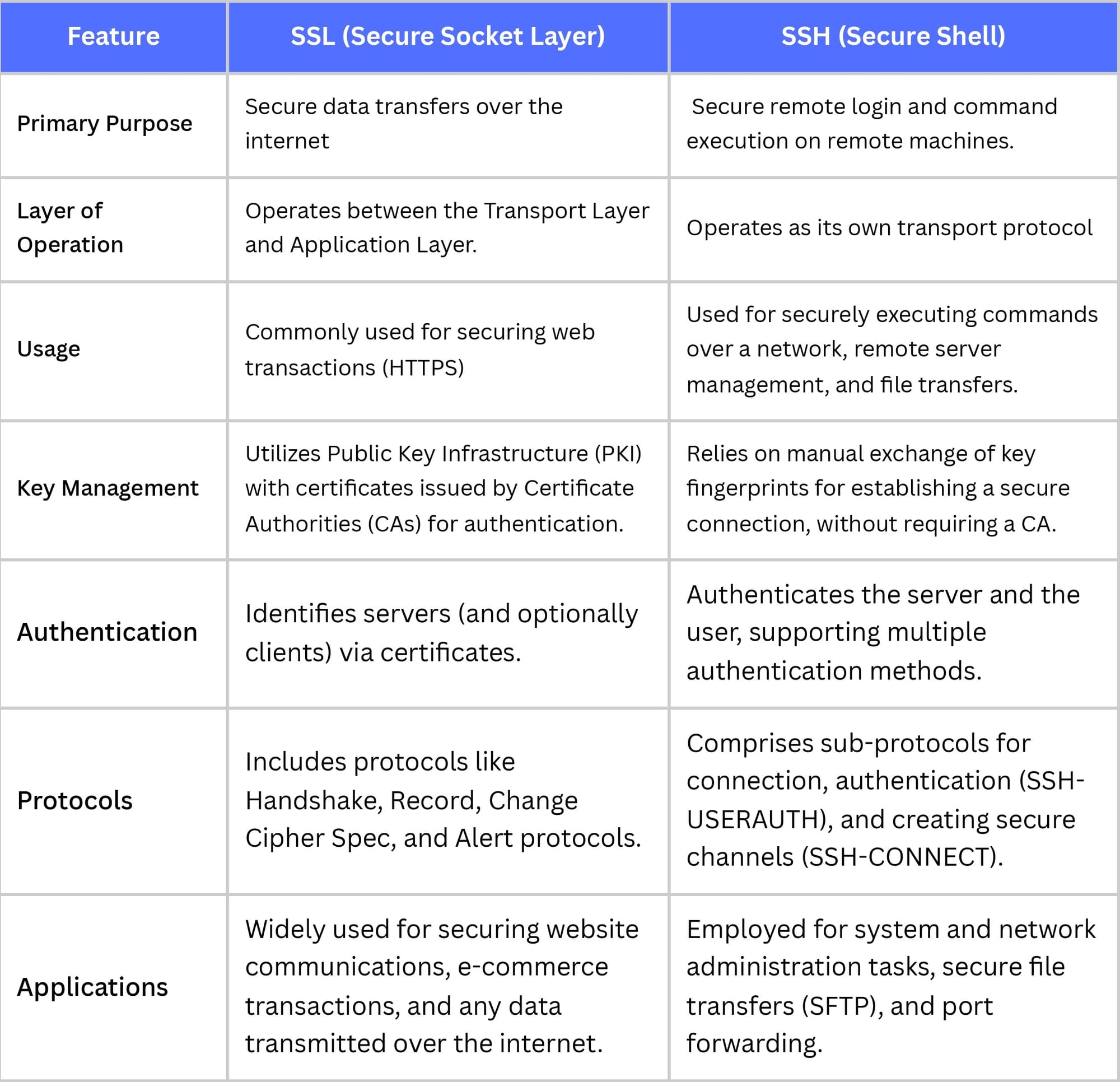
Similarities Between SSL and SSH
SSH and SSL/TLS are like having secret, secure conversations where you can be sure who you're talking to, that no one is listening in, and that the message stays the same from when you send it to when it's received.
Conclusion
SSL and SSH work in different spheres but their contribution collectively helps in securing communication on the Internet. Enables building trust in the security of online activities. As technology is increasing safeguarding is also important.
FAQ
Does SSH depend on SSL?
No, SSH (Secure Shell) does not depend on SSL (Secure Sockets Layer).
Similarities between SSL and TLS.
TLS is actually the successor to SSL.
Why SSH is better than HTTPS?
SSH (Secure Shell) and HTTPS (HTTP Secure) are both protocols used to secure communications over a network, but they are designed for different purposes and have different strengths. The reasons why one might consider SSH to be "better" than HTTPS depend on the specific use case.